Phishing Use Case
You can use Lookyloo to identify phishing attacks.
Phishing describes the attempt to obtain sensitive information often for malicious reasons, by masquerading as a trustworthy entity. A phishing website requests that users divulge sensitive information. Such attacks can incur substantial financial losses, in addition to inconveniencing and exposing users.
Phishing attacks are more common than one might think and are of critical concern to users, particularly in online businesses, and financial institutions.
Capture Phishing
Example 1
The following is an example of the capture that is displayed when a user visits the site getidsenvoieidss.com.
You can access the capture at this link.
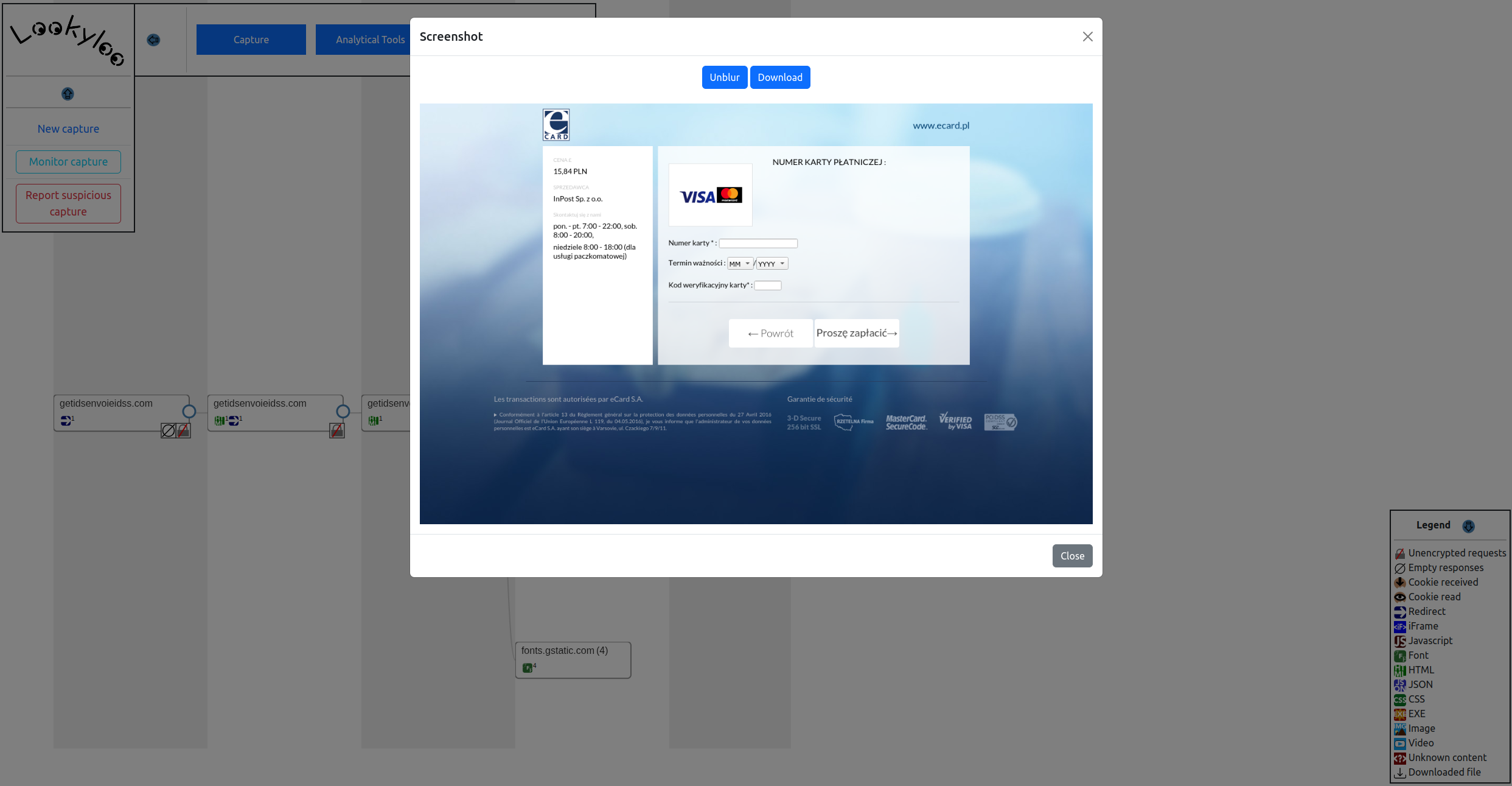
As represented by the lock icon, the site contains insecure requests (HTTP).
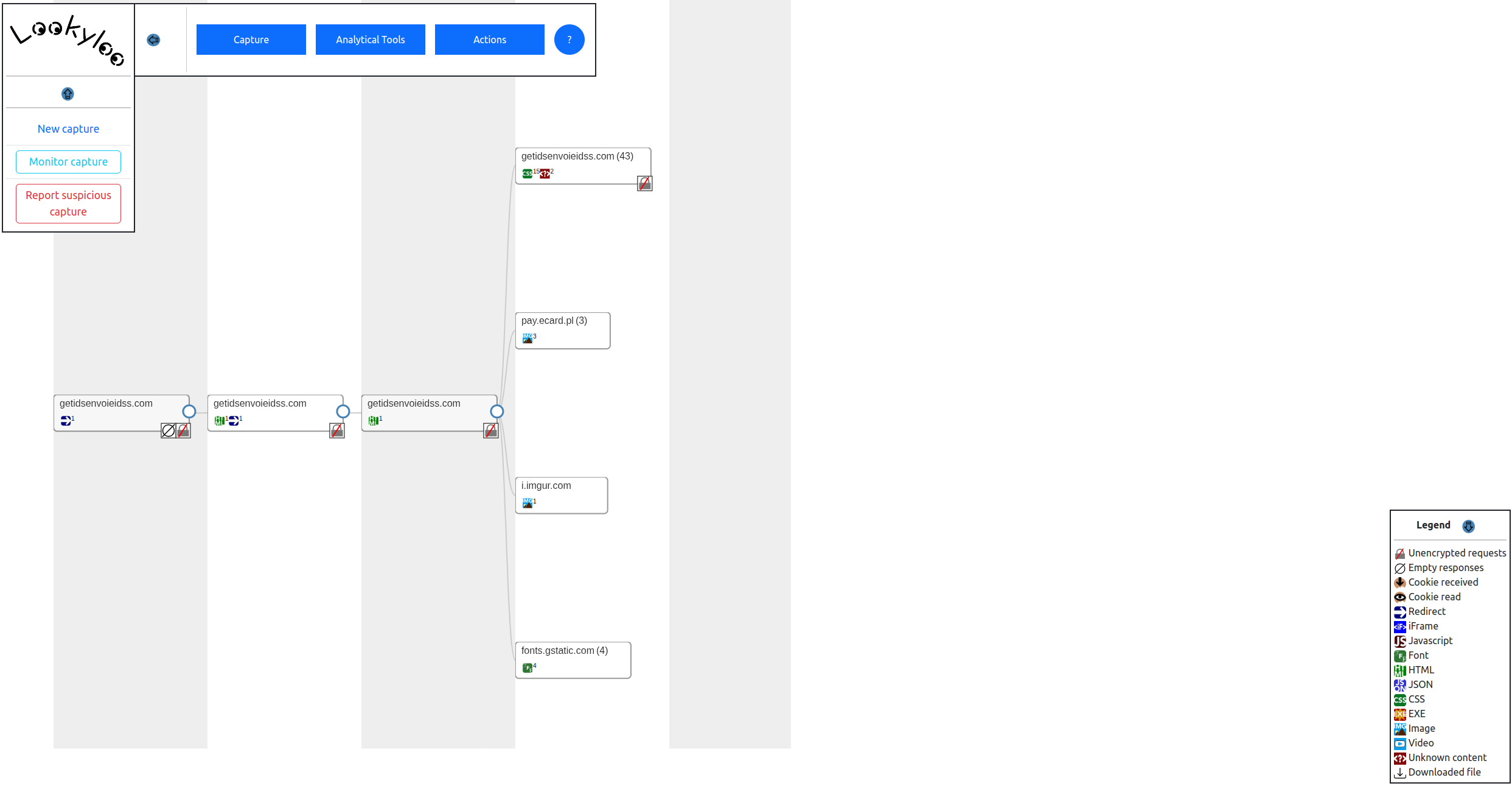
As indicated in the tree of domains, a user is redirected to a series of insecure sites, before a request is sent to pay.ecard.pl.
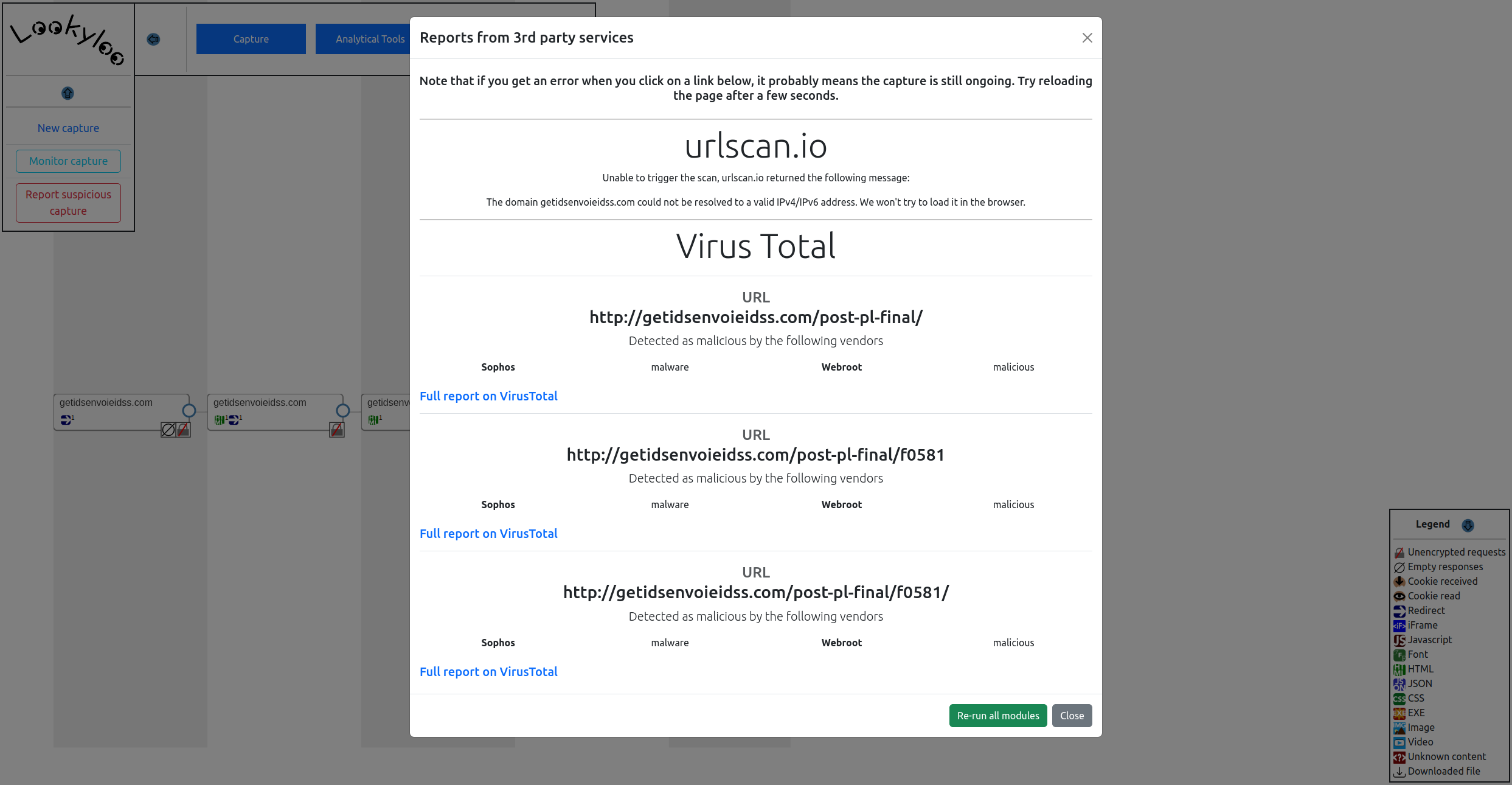
The capture can display any malicious activity as dectued from the vendor. When a user clicks Show third party reports in the menu, a Virus Totals report is rendered and available, which highlights that Sophos knows that this URL is malicious.
Example 2
On this site the user is redirected to an other phishing page. To access the redirect please see the following page.
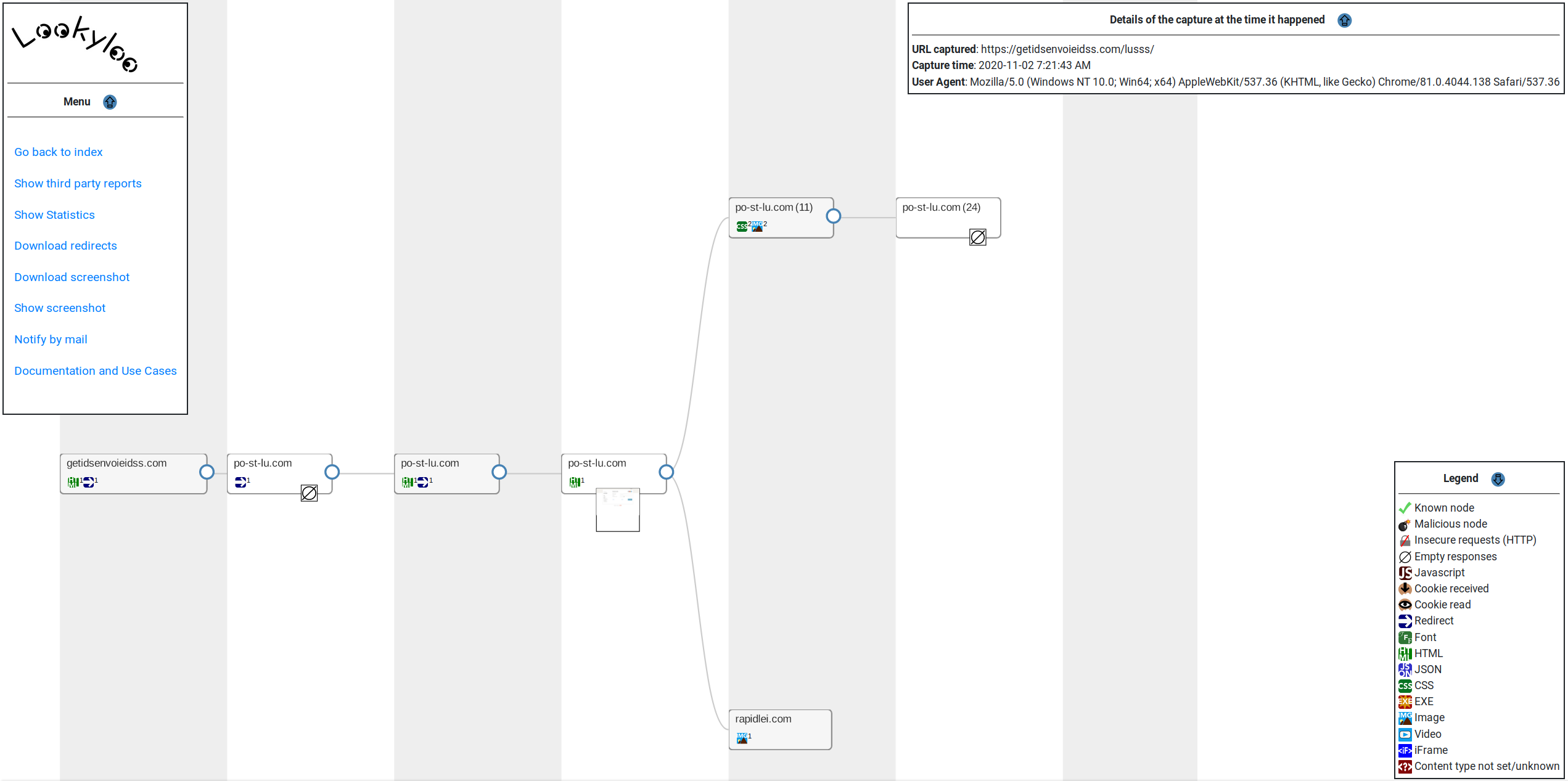
This one will also steal credit card information, but look like the luxemburgish post office.